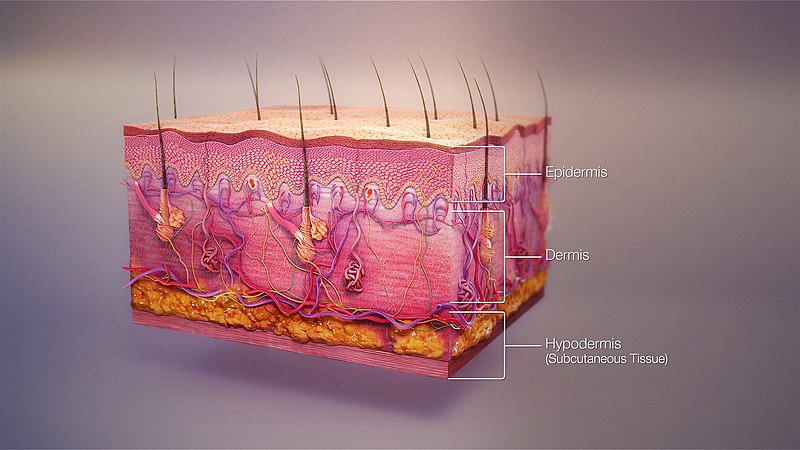
The Emerging Smart Grid: An Interconnected Power Distribution Network
We have all heard of the emerging technology known as the “smart grids” but what exactly does this mean for infrastructure development? What are the techniques and technologies used? And how will it affect the generation, transmission, distribution and consumption of energy and services?
Installing Advanced Metering Infrastructures (AMIs)
According to MIT Assistant Professor of Civil & Environmental Engineering and the Resilient Infrastructure Networks Lab (RESIL) Saurabh Amin, remote devices called Advanced Metering Infrastructures or AMIs are being deployed on the distribution and consumption side ie: commercial and residential consumers, allowing distribution utilities to have a more fine-grained monitoring of user consumption in real time. The result of this system is a streamlining of all aspects of the grid and in essence making it smart.
At the same time, this new equipment allows consumers to begin to participate in a wide variety of new savings programs offered by utilities which are called “Demand Response Schemes”. As grids become smarter consumers will find tune their demand for and use of electricity improving overall efficiency.
Inheriting IT Vulnerabilities
The infrastructure made up of AMIs are connected to communication networks which have been manufactured by IT companies and device manufacturers. If vulnerabilities are manufactured into this equipment they becomes part of the infrastructure, making it vulnerable as well.
Insufficient IT Security Tools & Malicious Actors
Today’s IT security tools such as encryption as well as network security protocols are applied to the electric grid but are not sufficient to protect it.
According to Amin, vulnerability is created at the point where cyber technology is combined with physical systems. The way to make the grid system secure, then, is to create algorithms that detect intrusions. Intrusions into the grid can occur at any one its levels, for example, a consumer trying to get free services from a distributor by hacking the system or small-scale producers of wind or solar over-reporting their output.
Other types of intrusions include people or organizations external to the grid who wish to intrude and cause failures throughout the system such as “load shedding” which reduces loads on the electric grid causing interruptions of electricity to consumers.
Monitoring The Cyber-Physical Dynamics
Amin and colleagues work to monitor the “Cyber-Physical Dynamics” of a grid by “encapsulating them into diagnostic tools” so that intrusions are detected in real time. Automatic control methods and Automatic Control Protection Devices (ACPD) are being developed that will trigger automatic responses such as triggering circuit breakers, etc.
For more on Amin’s projects visit his lab.
Grid Intrusion Diagnostic Algorithms
Amin takes the results from grid diagnostic algorithms and designs control methods to immediately trigger protection devices to limit the impact of failure due to intrusions. Most grids have a “failsafe” mode, which is built in but was intended only for shutdown due to damage from natural disasters or accidents, not from malicious security attacks.
Related articles on IndustryTap:
- Billionaire Developing Smart Grid For Medical Information
- Billions Of Dollars Spent On Smart Grid Modernization Projects Around The World
- $500 Billion Needed To Build US Smart Grid By 2030, Benefits Estimated At $2 trillion
- World’s Tallest Building, Burj Khalifa Running on ABB Custom Smart Grid
- Old Smartphones Get New Life as Rainforest Guardians
- Smart Voting Software Aims to Replace Politicians with Direct Democracy
- Military Smartphone App Orders Air Strikes, Saves Lives in Battle Zones
- The Story Behind Siemens: An Unrivaled Global Powerhouse
- The Energy Internet: Power Clouds
- Will Robots Rule Your World?
References and related links: